SSH (Secure Shell) is an essential protocol for securely accessing remote systems, allowing users and administrators to manage servers, systems, and devices over an encrypted connection. However, if not properly secured, SSH can be an entry point for attackers. This guide will cover the best practices for securing SSH and safeguarding remote access, including tips for Android users who rely on SSH for mobile system management.
What Is SSH?
SSH is a cryptographic network protocol used for securing remote communication between a client and a server. It protects the connection by encrypting data and authenticating both the client and the server. The protocol is widely used for managing systems, executing commands, and transferring files securely.
However, improper configurations or weak security practices can expose SSH connections to potential attacks. By following the recommended SSH security best practices, you can minimize these risks.
Why SSH Security Matters
Without proper security, SSH can become a gateway for brute force attacks, credential theft, and other malicious activities. Securing your SSH setup helps protect sensitive data and ensures safe system administration.
Key Vulnerabilities in SSH
- Brute force attacks: Attackers try multiple username and password combinations to gain unauthorized access.
- Credential theft: If passwords or private keys are compromised, attackers can use them to gain access.
- Man-in-the-Middle (MitM) attacks: Intercepted SSH sessions can lead to sensitive information leaks if connections are not properly authenticated.
1. Disable Root Login
One of the first steps to improve SSH security is to disable root login. Logging in as the root user gives full access to the system, making it a prime target for attackers.
How to Disable Root Login
Edit the SSH configuration file (/etc/ssh/sshd_config) and set the following parameter:

This ensures that no one can log in as the root user over SSH. Instead, users can log in with a regular account and use sudo for administrative tasks.
2. Use Strong Authentication Methods
SSH offers multiple authentication methods, and it’s essential to opt for the strongest ones to minimize the attack surface.
Use Public Key Authentication
Public key authentication is more secure than password-based logins. It relies on a pair of cryptographic keys: one public and one private. The private key remains securely on your device, while the server stores the public key.
To enable public key authentication, generate a key pair on the client and add the public key to the server’s ~/.ssh/authorized_keys file.
Disable Password-Based Authentication
Since passwords are susceptible to brute force attacks, it’s a good idea to disable password-based authentication entirely. This forces all users to use keys, which are far more secure.
In the sshd_config file, set:

3. Change the Default SSH Port
By default, SSH listens on port 22, which is commonly targeted by attackers. Changing the SSH port to a non-standard one can reduce exposure to brute force attacks.
In the sshd_config file, modify the port setting:

Choose a port number that is not commonly used but still accessible.
4. Use SSH Key Passphrases
SSH keys are highly secure, but adding a passphrase to the private key adds an extra layer of protection. In case your private key is stolen, the attacker would still need the passphrase to access it.
When generating the key pair with the ssh-keygen command, make sure to set a strong passphrase.
5. Limit User Access
Only allow necessary users to connect via SSH. You can limit access by specifying which users or groups are permitted to log in.
In sshd_config, add:

This restricts SSH access to only those specified users.
6. Enable Two-Factor Authentication (2FA)
Adding two-factor authentication (2FA) enhances SSH security by requiring an additional verification step, such as a time-based one-time password (TOTP).
You can set up 2FA using Google Authenticator or similar tools. This is particularly useful for Android users who manage servers remotely via mobile devices.
7. Set Idle Timeout Intervals
If users forget to log out of their SSH sessions, leaving them open for long periods, they can become vulnerable to unauthorized access. Setting a timeout disconnects idle sessions automatically.
In sshd_config, add:

This configuration will disconnect users after 5 minutes of inactivity.
8. Use a Firewall to Limit SSH Access
A firewall can be configured to restrict SSH access to specific IP addresses or ranges, reducing the exposure of your SSH server to attackers.
On Linux Systems
You can use iptables or ufw to create firewall rules that limit SSH access to trusted IP addresses:
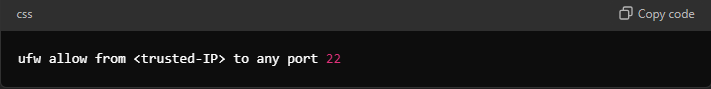
This rule ensures that only specified IP addresses can access your SSH server.
9. Regularly Update SSH and Server Software
Security vulnerabilities are often discovered in software, including SSH servers and clients. Regular updates are crucial to patching known vulnerabilities.
Make it a habit to update your operating system and SSH server software:

10. Use Fail2Ban for Brute Force Protection
Fail2Ban is a tool that monitors server logs for failed login attempts and blocks suspicious IP addresses after a predefined number of attempts.
Install and configure Fail2Ban on your system:

Once installed, Fail2Ban automatically protects your SSH server from brute force attacks.
Best SSH Practices on Android
SSH isn’t limited to desktops or servers. Android users can use SSH clients like JuiceSSH or Termux to manage remote systems on the go. Here are a few best practices for using SSH on Android devices:
- Use a Strong Passphrase: When storing private keys on your Android device, ensure they are encrypted with a strong passphrase.
- Limit Access: Disable root access via SSH on your Android device, and set up a non-root user account for connections.
- Enable 2FA: Two-factor authentication is especially useful on mobile devices to protect against unauthorized access.
Conclusion
Securing SSH access is crucial for protecting sensitive data and remote systems. By following these SSH security best practices—from disabling root login to using strong authentication and firewall rules—you can minimize the risk of unauthorized access. For Android users managing systems remotely, special considerations, such as using SSH clients and enabling 2FA, help ensure safe and secure remote access.