In today’s digital landscape, securing your Linux system is paramount to protect against threats and vulnerabilities. Whether you are managing a server or a personal computer, implementing effective hardening techniques can significantly enhance your system’s security. This article outlines essential Linux hardening techniques to help you secure your system against potential attacks.
1. Keep Your System Updated
Regular updates are the first line of defense against vulnerabilities. Keeping your system and software up-to-date ensures you have the latest security patches and features.
- Command to update your system:

- Automate updates: You can set up unattended upgrades to automatically install security updates.
2. Minimize Installed Packages
Reducing the number of installed packages minimizes the attack surface. Uninstall any software or services that are not needed.
- Command to remove a package:

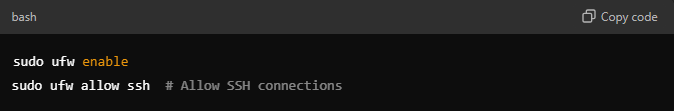
3. Configure a Firewall
A firewall acts as a barrier between your system and potential threats. Configuring a firewall helps control incoming and outgoing traffic based on predetermined security rules.
- Using UFW (Uncomplicated Firewall):
4. Use Strong Passwords and Authentication
Ensure that all user accounts have strong passwords. Consider using password managers to generate and store complex passwords.
- Implement Two-Factor Authentication (2FA): 2FA adds an additional layer of security by requiring a second form of verification.
5. Disable Unused Services
Disabling services that are not in use can help reduce vulnerabilities.
- List active services:

- Disable unnecessary services:

6. Secure SSH Access
SSH (Secure Shell) is commonly used for remote administration. Securing SSH access is crucial to prevent unauthorized logins.
- Steps to secure SSH:
- Change the default SSH port (22) to another number.
- Disable root login by modifying the
/etc/ssh/sshd_configfile.

- Use SSH key authentication instead of passwords.
7. Implement File System Permissions
Properly configured file permissions ensure that only authorized users can access or modify sensitive files.
- Set permissions using chmod:

- Regularly audit permissions: Use commands like
findto check for incorrect permissions.
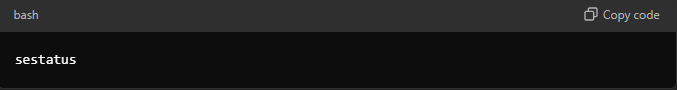
8. Use SELinux or AppArmor
SELinux and AppArmor are security modules that provide an additional layer of security by enforcing access control policies.
- Check SELinux status:
- Install and enable AppArmor:

9. Log Monitoring
Regularly monitoring logs helps detect suspicious activity. Tools like logwatch or fail2ban can automate the monitoring process.
- Install logwatch:

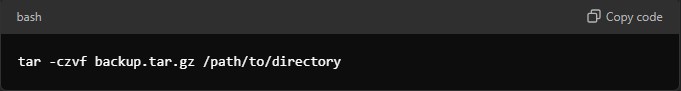
10. Backup Regularly
Regular backups are essential for recovering from data loss incidents. Use tools like rsync or tar for backup.
- Example command to create a backup:
Conclusion
Implementing these essential Linux hardening techniques can greatly enhance your system’s security. Regularly updating your software, minimizing installed packages, configuring a firewall, and using strong authentication methods are critical steps in securing your Linux environment. By taking these precautions, you can significantly reduce the risk of security breaches and ensure the integrity of your system.